When it comes to ransomware, most organizations feel a sense of reassurance knowing they have backups in place. But here’s the hard truth: having backups isn’t the same as being able to recover. And that myth can be a costly one. Ransomware Targets Your Weakest Links—Your Storage Modern ransomware doesn’t just encrypt files—it hunts for structural weaknesses in your environment. And most businesses unknowingly provide plenty of them. From on-prem… Read More
Why Traditional Backups Fail Against Ransomware—and What to Do Instead
As cyberattacks grow more advanced, achieving digital resilience requires more than a traditional ‘set-it-and-forget-it’ backup approach. Legacy methods no longer provide the protection necessary against today’s sophisticated threats—especially ransomware. To safeguard your data and ensure business continuity, you need a modern backup strategy that encompasses cyber resilience as an integral part of a holistic approach, ensuring your systems can withstand and recover from attacks. The Limitations of Traditional Backups Traditional… Read More
The Backup Fallacy: Why Data Protection Alone Won’t Stop Ransomware
Is data protection enough to stop ransomware in its tracks? Not quite. In this TECH Talk, you’ll discover why air-gapped backups, immutability, and access controls are key to recovery. Plus, we’ll show how IT and security teams can join forces—because simply backing up your data isn’t enough to outsmart today’s cybercriminals. Join our livestream on Thursday, 9/26. Co-hosts: Shahin Pirooz, DataEndure’s CTO & CISO Kirstin Burke, DataEndure’s CMO
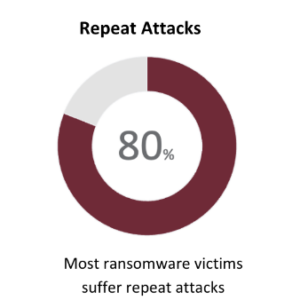
Why 80% of Ransomware Victims Suffer Repeat Attacks
In the realm of cybersecurity, the adage “lightning never strikes the same place twice” doesn’t apply. Organizations that have suffered one cyberattack are commonly targeted again, regardless of company size or industry. Ransomware by the Numbers Why Do Attackers Repeatedly Target the Same Company? The first cyberattack yields detailed insights into a company’s security architecture and response protocols. This intel becomes invaluable for orchestrating subsequent attacks that are often more… Read More