Each October, the US Department of Homeland Security observes National Cybersecurity Awareness Month, “a collaborative effort between government and industry to raise awareness about the importance of cybersecurity and to ensure that all Americans have the resources they need to be safer and more secure online.” In today’s information era, data security is everyone’s responsibility. Whether you’re a small company delivering professional services to a local clientele, or an enterprise… Read More
Are you prepared for the 2020 California Consumer Privacy Act (CCPA)?
You don’t have to be a security expert to notice the rising rate of data breaches making national and global news these days. In 2018, no less than 6500 separate incidents exposed a total of 5 billion records, and 2019 is forecast to eclipse those staggering figures. The reaction to these events has been relatively swift. In the first half of 2018, regulators for the European Union enacted GDPR (General… Read More
Part 2: The Solution to Cybersecurity’s Biggest Challenge
Last month, we looked back at Fortune’s Brainstorm Tech 2019 in Aspen, Colorado. During a lunchtime cybersecurity roundtable, the featured speakers were asked a two-part question: What’s the biggest challenge the world faces with respect to cybersecurity today? And what is the solution? We posed the first question to Shahin Pirooz, CTO and CISO at DataEndure in our previous post. This month we will look at the solution. For decades,… Read More
Part 1 of 2: The Biggest Cybersecurity Challenge Facing the World Today
Fortune’s Brainstorm Tech 2019 was held recently in Aspen, Colorado. During a lunchtime cybersecurity roundtable, the session’s featured speakers were asked a two-part question: What’s the biggest challenge the world faces with respect to cybersecurity today? And what is the solution? We posed the same two questions to Shahin Pirooz, CTO and CISO at DataEndure. With over two decades leading technology teams and having been deeply immersed in the evolution… Read More
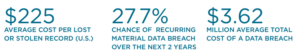
Lessons from Verizon’s 2019 Data Breach Investigations Report
Verizon’s 2019 Data Breach Investigations Report (DBIR) was published last week and continues to be one of the most valuable annual “state of the union” reports in the security. This year’s report is the most extensive to date, with 73 contributors and an analysis of 41,686 security incidents including 2,013 confirmed breaches. At DataEndure, we use the insight from this report to validate what we are seeing in the market,… Read More
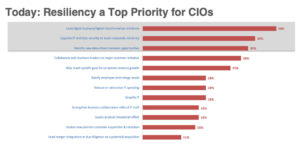
Developing Resilience to Withstand Cyberattacks has Never Been More Important
Highlights from DataEndure’s recent Keynote and Cocktails event featuring Shahin Pirooz, CTO/CISO, DataEndure and Jeff Gallager, VP Events, IDC Companies are increasingly dependent on technology to drive innovation and their digital transformation strategies. With people and data everywhere the simple act of being connected – whether it’s through mobile devices, IoT, or other areas – creates risk. And where there is risk, there is opportunity for attack. When we say… Read More
Hiring & Retaining Cyber Security Talent is a Top Concern for CEOs
In a recent global survey, The Conference Board found that U.S. CEOs rank cyber security as their #1 external concern and acquiring/retaining talent as their #1 internal concern for 2019. With high-profile data breaches becoming more and more common, the fear is warranted. And for organizations looking to hire and retain cyber security experts, the intersection of these leading concerns is well, concerning. “As global competition increases while the pool of… Read More
7 Questions You Need to Be Able to Answer After a Cybersecurity Event
In the past 2 weeks, there have been three (more) high-profile cybersecurity breaches disclosed, impacting three very different organizations – and hundreds of millions of individuals worldwide. Marriott reported hackers have had access to the reservation systems of many of its hotel chains for the past four years, a breach that exposed private details of up to 500 million customers; Quora, the crowdsourced question and answer site, reported the potential exposure of 100 million users… Read More
Aligning Security and Compliance on a Budget
Excerpts from NorCal CyberSecurity Summit on September 5, 2018; session presented by Shahin Pirooz, CTO/CISO of DataEndure. You can watch the full presentation here. More and more organizations and agencies are getting attacked on a daily basis, with newer threat vectors emerging faster than ever and even new business models developing to take advantage of the extremely lucrative cybercrime market. The city of Atlanta serves as a recent example (and warning)… Read More
To SIEM or not to SIEM?
From ransomware to DDoS attacks, companies are under siege. To effectively mitigate breach risk today requires enormous expertise, resources and budget. Companies are losing more each year on cybercrime than they are spending to prevent it. Security Incident and Event Management (SIEM) tools are one example of how organizations are attempting to combat the problem of cybercrime. A SIEM scans your network and provides visibility into suspicious/illegitimate activity. Unfortunately, as… Read More
- « Previous Page
- 1
- …
- 7
- 8
- 9
- 10
- Next Page »